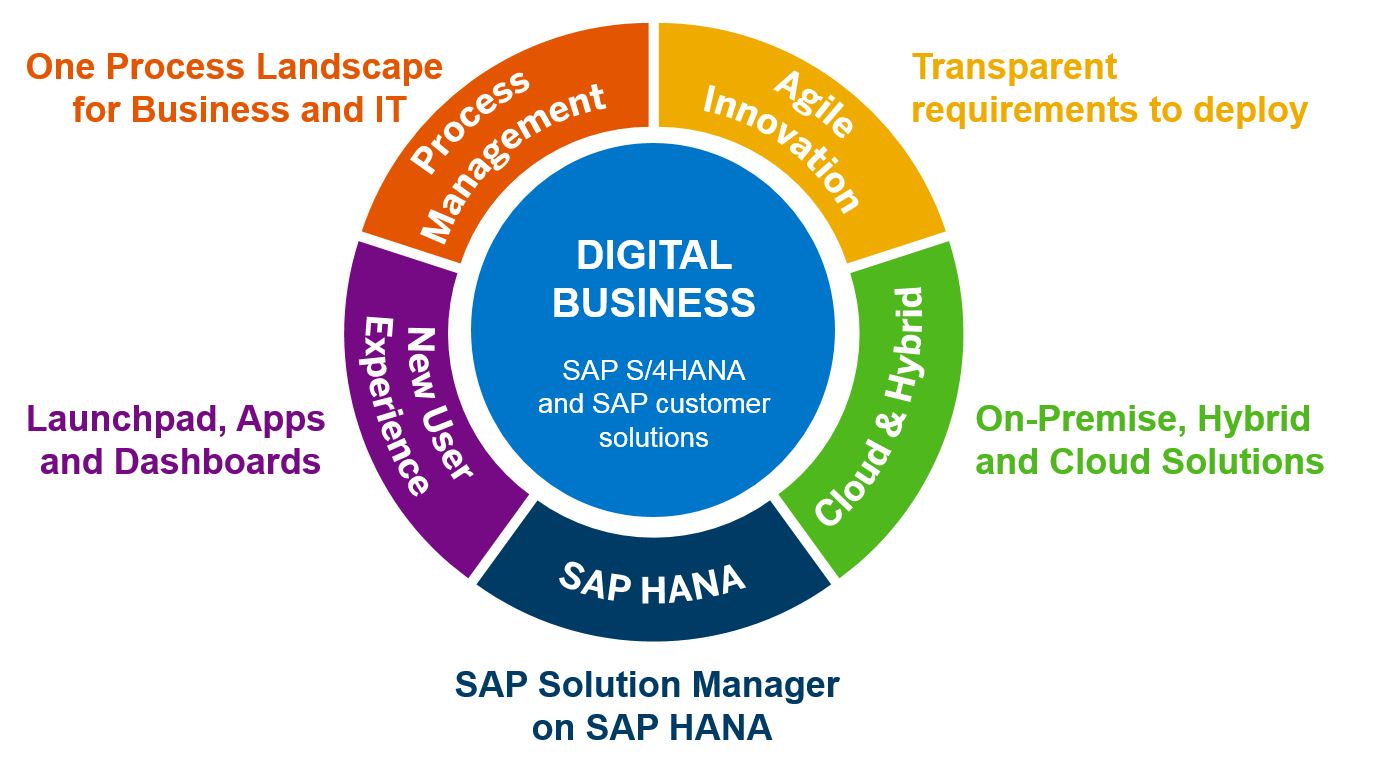
What is Data Classification Policy

1. Purpose
Explain why information data classification policy must be done and also what benefits it need to bring. The function of this policy is to develop a framework for classifying information based upon its sensitivity, worth and urgency to the company, so delicate business and also client data can be safeguarded properly.
2. Scope
Specify the types of data that have to be classified as well as specify who is in charge of appropriate information data classification policy, security and handling.
This policy puts on any kind of type of information, including paper files and also electronic data kept on any kind of sort of media. It relates to every one of the company’s workers, as well as to third-party agents accredited to access the data.
3. Roles and Responsibilities
Explain the roles and responsibilities associated with the data classification policy initiative. Departments ought to designate people that will certainly be in charge of performing the duties connected with each of the duties.
Information owner– The individual who is eventually responsible for the data and also details being gathered and kept by his or her division or division, usually a participant of senior management. The information owner will resolve the following:
Evaluation as well as categorization-– Review and also classify data as well as info collected by his or her division or division
Project of information category labels— Appoint data classification labels based upon the data’s potential impact degree
Information compilation— Ensure that data assembled from several resources is classified with at the very least the most safe and secure classification level of any type of independently identified information
Data category coordination— Ensure that data shared between departments is consistently classified and secured
Information category compliance (in conjunction with information custodians)– Make certain that info with high and also moderate impact degree is protected based on federal or state guidelines and standards Information access (combined with data custodians)– Develop information access guidelines for every information data classification policy label
Information custodians— Technicians from the IT department or, in larger companies, the Information Security workplace. Information custodians are in charge of preserving and supporting the systems, data sources and web servers that save the organization’s information. Additionally, this role is accountable for the technological release of all of the rules state by information owners and for making certain that the rules applied within systems are functioning. Some particular information custodian obligations consist of:
Gain access to control— Ensure that proper gain access to controls are executed, kept track of and also audited based on the information category labels appointed by the information proprietor
Audit reports— Submit an annual report to the data owners that deals with schedule, integrity and also discretion of identified information
Data backups— Perform routine back-ups of state data
Information recognition— Periodically verify information integrity
Information reconstruction— Restore data from backup media
Conformity— Fulfill the information requirements defined in the company’s safety and security policies, criteria and standards relating to info protection and information protection
Display task— Monitor and also document information activity, consisting of information on that accessed what data
Safe and secure storage— Encrypt delicate data at rest while in storage space; audit storage location network (SAN) administrator task and review gain access to logs frequently
Data classification compliance (combined with data proprietors)— Ensure that information with high as well as moderate impact level is secured in accordance with government or state regulations and standards
Information access (together with data proprietors)— Develop data access standards for every information classification label
Information customer— Person, company or entity that interacts with, accesses, uses or updates information for the purpose of performing a job licensed by the information proprietor. Data customers have to use data in a manner constant with the purpose intended, and also adhere to this policy and all plans appropriate to information make use of.
4. Data Classification Procedure
Explain each data category treatment step by step. Detail that performs each action, just how information is evaluated for level of sensitivity, what to do when data does not fit a recognized data classification policy and so on.
Instance of a detailed treatment:
1. Information proprietors evaluate each item of data they are accountable for and determine its overall effect degree, as adheres to:
If it matches any one of the predefined kinds of limited info detailed in Appendix A, the data owner assigns it a general effect degree of “High.”. If it does not match any of the predefined key ins Appendix A, the information owner ought to establish its info kind and also impact levels based upon the support supplied in Sections 5 and also 6 of this document, as well as NIST 800-600 Volume 2. The highest of the three effect levels is the total effect degree.
If the details kind as well as general effect degree still can not be figured out, the data owner should work with the data custodians to deal with the question.
2. The data owner appoints each item of data a classification tag based on the overall effect degree:.
- Overall influence levelClassification label.
- HighRestricted.
- ModerateConfidential.
- Low Public.
3. The information proprietor documents the category label as well as overall influence degree for every piece of information in the official data classification table, either in a database or theoretically.
4. Data custodians apply ideal safety and security controls to safeguard each item of information according to the classification tag and also total impact degree tape-recorded in the main information category table.
Example of a basic procedure:.
- Information proprietors review and also appoint each piece of data they possess an info kind based on the classifications in NIST 800-600 Volume 1.
- Information proprietors assign each piece of data a potential impact level for every of the security purposes (confidentiality, integrity, availability), making use of the guide in Section 6 of this paper. The highest possible of the three is the general effect level.
- Information proprietors designate each piece of data a category tag based upon the general effect level:.
- Overall impact levelClassification tag.
- HighRestricted.
- ModerateConfidential.
- Low Public.
- Information proprietors videotape the influence level as well as category tag for every item of data in the data category table.
- Data custodians apply details security controls to each item of information according to its classification label and general effect level.
5. Data Classification Guideline.
Create a table that explains each kind of information possession the firm stores, information the impact of each of the 3 safety and security purposes, as well as specifies the influence levels and also data classification policy to be assigned to every kind of asset.
Utilize this table to identify the total effect level as well as category tag for lots of info possessions commonly made use of in the company.
| Federal Budget Planning Documents | |||
| Federal budget planning documents state the potential expenses for the following year. They include data about partners and suppliers, as well as analytical and research data. | |||
| Information Types | |||
| Funds Control | Funds Control documents include information about the management of the federal budget process, including the development of plans and useprograms, budgets, and performance outputs, as well as information about financing federal programs and operations through appropriation and apportionment of direct and reimbursable spending authority, fund transfers, investments and other mechanisms. | ||
| Security Objectives | Confidentiality Impact | Integrity Impact | Availability Impact |
| Impact Description | Unauthorized disclosure of funds control information (particularly budget allocations for specific programs or program elements) can be seriously detrimental to government interests in procurement processes. In many instances, such unauthorized disclosure is prohibited by executive order or by law. Premature release of drafts of funds control information can yield advantages to competing interests and seriously endanger agency operations or even agency mission. | Funds control activities are not generally time-critical. An accumulation of small changes to data or deletion of small entries can result in budget shortfalls or cases of excessive obligations or disbursements. | Funds control processes are generally tolerant of delay. Typically, disruption of access to funds control information can be expected to have only a limited adverse effect on agency operations, agency assets or individuals. |
| Impact Level | Moderate | Moderate | Low |
| Overall Impact Level | Moderate | ||
| Data Classification Label | Confidential | ||
6. Influence Level Determination.
Supply a table that will certainly aid data owners establish the influence level for every item of information by describing the safety and security objectives you wish to attain as well as exactly how failing to acquire each purpose would certainly affect the organization.
Use this table to analyze the potential impact to the firm of a loss of the discretion, stability or accessibility of an information possession that does not fall under any of the details kinds explained in Section 5 and NIST 800-600 Volume 2.
| Security Objective | Potential Impact | ||
| Low | Moderate | High | |
| Confidentiality. Restrict access to and disclosure of data to authorized users in order to protect personal privacy and secure proprietary information. | Unauthorized disclosure of the information is expected to have limited adverse effects on operations, organizational assets, or individuals. | Unauthorized disclosure of the information is expected to have a serious adverse effect on operations, organizational assets, or individuals. | Unauthorized disclosure of the information is expected to have a severe or catastrophic adverse effect on operations, organizational assets, or individuals. |
| Integrity. Guard against improper modification or destruction of data, which includes ensuring information nonrepudiation and authenticity. | Unauthorized modification or destruction of the information is expected to have a limited adverse effect on operations, assets, or individuals.
| Unauthorized modification or destruction of the information is expected to have a serious adverse effect on operations, assets, or individuals. | Unauthorized modification or destruction of the information is expected to have a severe or catastrophic adverse effect on operations, assets, or individuals. |
| Availability. Ensure timely and reliable access to and use of information. | Disruption of access to or use of the information or information system is expected to have a limited adverse effect on operations, assets, or individuals. | Disruption of access to or use of the information or information system is expected to have a serious adverse effect on operations, assets, or individuals. | Disruption of access to or use of the information or information system is expected to have a severe or catastrophic adverse effect on operations, assets, or individuals. |
7. Appendix A data classification policy.
Define the types of details that ought to automatically be classified as “Limited” and assigned an influence level of “High.” Having this checklist will certainly make the information data classification policy process much easier for data owners.
Types of Info that Need To be identified as “Restricted”.
Verification information.
Authentication information is information made use of to show the identification of a specific, system or service. Examples include:
- Passwords.
- Shared keys.
- Cryptographic personal tricks.
- Hash tables.
Electronic Protected Health Info (ePHI).
ePHI is specified as any secured health details (PHI) that is kept in or sent by electronic media. Electronic media consists of computer hard disks as well as detachable or mobile media, such as a magnetic tape or disk, optical disk, or electronic flash memory card.
Transmission is the activity or exchange of details in digital type. Transmission media includes the internet, an extranet, rented lines, dial-up lines, exclusive networks, as well as the physical activity of detachable or easily transportable digital storage space media.
Repayment Card Details (PCI).
Repayment card information is defined as a credit card number in combination with several of the adhering to data components:.
- Cardholder name.
- Service code.
- Expiration date.
- CVC2, CVV2 or CID worth.
- PIN or PIN block.
- Materials of a charge card’s magnetic red stripe.
Personally Identifiable Info (PII).
PII is specified as a person’s first name or very first preliminary and also last name in mix with one or more of the complying with data aspects:.
- Social security number.
- State-issued chauffeur’s certificate number.
- State-issued identification card number.
- Financial account number in mix with a security code, gain access to code or password that would certainly permit access to the account.
- Clinical and/or health insurance details.
8. Revision History data classification policy
Make certain to track all changes to your data classification policy.
| Version | Published | Author | Description |
|---|---|---|---|
| 0.1 | 01/01/2018 | John Smith | Original |
Check out over other articles like: